Data Privacy Day just passed and with World Backup Day around the corner, we’ve prepared 10 data security tips to help you secure your Synology devices against online threats.
The past years have seen a dramatic escalation in cybersecurity threats. According to a report by The New York Times, more than 200,000 organizations were attacked with ransomware in 2019, a 41% rise from the year before.
To help you protect yourself, we’ve compiled a list of important data security settings that are often overlooked. At the end we’ve included bonus tips that could help you ensure data integrity — another pillar of data protection.
Note: Most of the settings listed below can only be accessed and modified by a user account with administrative rights.
 Tip 1: Stay up to date and enable notifications
Tip 1: Stay up to date and enable notifications
We release DSM updates regularly to provide functional and performance enhancements, and to resolve product security vulnerabilities.
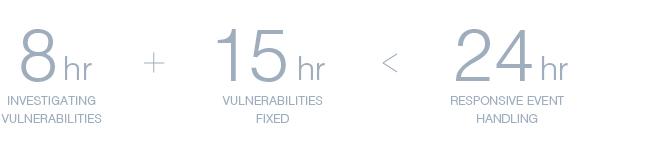
Whenever a security vulnerability arises, our Product Security Incident Response Team (PSIRT) will conduct an assessment and investigation within 8 hours and release a patch within the next 15 hours to help prevent potential damage from zero-day attacks.
For most users, we strongly recommend that you set up automatic updates to have the latest DSM updates installed automatically.*
Many Synology devices have the option to run Virtual DSM inside Virtual Machine Manager, to create a virtualized version of the DSM operating system. Use Virtual DSM to create a staging environment, then replicate or try to reproduce your production environment within it. Perform an upgrade test by installing the latest DSM version on your Virtual DSM and verify key functionality that your current deployment requires before proceeding with the update in your main environment.
Another important thing to consider is staying on top of things as they occur. Set up notifications on your Synology NAS and get notified by email, SMS, on your mobile device, or through your web browser when specific events or errors occur. If using Synology’s DDNS service, you can choose to be notified when external network connectivity is lost. Immediately acting upon notifications for storage volumes running out of space, or when a backup and restoration task fails is an important part of ensuring your data’s long-term security.
We also encourage you to set up your Synology Account to receive our NAS and security advisory newsletters to keep up with the latest security and feature updates.
* Automatic update only supports minor DSM updates. Major updates require manual installation.
 Tip 2: Run Security Advisor
Tip 2: Run Security Advisor
Security Advisor is a pre-installed application that can scan your NAS for common DSM configuration issues, giving you suggestions for what you might need to do next to keep your Synology NAS safe. For example, it can detect common things such as leaving SSH access open, if any abnormal log in activities are occurring, and if DSM system files have been modified.
 Tip 3: Basic DSM security features to setup
Tip 3: Basic DSM security features to setup
You can configure a number of security settings in the Control Panel > Security tab to secure your user accounts.
![]() IP Auto Block
IP Auto Block
Open Control Panel and go to Security > Auto Block. Enable auto block to automatically block IP addresses of clients that fail to sign in within a specified number of times and period. Administrators can also blacklist specific IP addresses to prevent potential brute-force or denial-of-service attacks.
Configure the amount of tries based on the usage environment and type of users that your device will reguarly service. Keep in mind that most homes and businesses will only have one external IP address for their users and that IP addresses are often dynamic and will change after a certain number of days or weeks.
![]() Account Protection
Account Protection
While Auto Block blacklists IP addresses that have failed one too many authentication attempts, Account Protection protects user accounts by blocking untrusted clients’ access.
Go to Control Panel > Security > Account Protection. You can enable Account Protection to shield accounts from untrusted clients after a set number of failed signins. This improves the security of your DSM and reduces risk of accounts falling prey to brute-force attacks from distributed attacks.
![]() Enable HTTPS
Enable HTTPS
With HTTPS enabled, you can encrypt and secure the network traffic between your Synology NAS and connected clients, which protects against common forms of eavesdropping or man-in-the-middle attacks. Go to Control Panel > Network > DSM Settings. Tick the checkbox for Automatically redirect HTTP connections to HTTPS. You will now connect to DSM via HTTPS. In the address bar, you’ll notice that your device’s URL starts with “https://” instead of “http://”. Note that the default port number for https is 443, while http by default uses port 80. If you had certain firewall or network settings in place before, you may need to update them.
![]() Advanced: Customize Firewall rules
Advanced: Customize Firewall rules
A firewall serves as a virtual barrier that filters network traffic from external sources according to a rule set. Go to Control Panel > Security > Firewall to set up firewall rules to prevent unauthorized sign-in and control service access. You can decide whether to allow or deny access to certain network ports by specific IP addresses, a good way to for example, allow remote access from a specific office or to only allow access to a specific service or protocol.
 Tip 4: HTTPS Part 2 – Let’s Encrypt
Tip 4: HTTPS Part 2 – Let’s Encrypt
Digital certificates play a key role in enabling HTTPS, but are often expensive and difficult to maintain, especially for non-business users. DSM has built-in support for Let’s Encrypt, a free and automated certificate issuing organization, to enable anyone to easily secure their connections.
If you already have a registered domain or are using DDNS, go to Control Panel > Security > Certificate. Click Add a new certificate > Get a certificate from Let’s Encrypt, for most users, you should check “Set as default certificate”*. Enter your domain name to get a certificate.
Once you’ve gotten a certificate, make sure all your traffic goes through HTTPS (as listed in Tip #3).
* If you have setup your device to provide services through multiple domains or sub-domains, you will need to configure which certificate is used by each service in Control Panel > Security > Certificate > Configure
 Tip 5: Disable the default admin account
Tip 5: Disable the default admin account
Common administrator usernames can make your Synology NAS vulnerable to malicious parties that employ brute-force attacks that use common username and password combinations. Avoid common names such as “admin”, “administrator”, “root”* when setting up your NAS. We recommend that you also set a strong and unique password right after setting up your Synology NAS and to disable the system default admin account**.
If you are currently logging in using the “admin” user account, go to Control Panel > User and create a new administrative account. Then log in using the new account and disable the system default “admin”.
* “root” is not allowed as a username.
** If set up using a username other than “admin”, the default account will already be disabled.
 Tip 6: Password Strength
Tip 6: Password Strength
A strong password protects your system from unauthorized access. Create a complex password that incorporates mixed-case letters, digits, and special characters in a way that only you can remember.
Using a common password for many accounts is also an invitation to hackers. If an account is compromised, hackers can easily take control of your other accounts. This happens on a regular basis for websites and other service providers. We recommend signing up with public monitoring services such as Have I Been Pwned or Firefox Monitor.
If you have trouble memorizing complex and unique passwords for different accounts, a password manager (such as 1Password, LastPass, or Bitwarden) could be your best solution. You only have to memorize one password – a master password – and the password manager will help you create and fill in sign-in credentials for all your other accounts.
If you admininister a Synology NAS that handles authentication*, you can customize user password policy to tighten password security requirments for all new user accounts. Go to Control Panel > User > Advanced and tick the Apply password strength rules checkbox under the Password Settings section. The policy will be applied to any user who creates a new account.
* Similar options are also available within the LDAP Server and Directory Server packages.
 Tip 7: 2-step verification
Tip 7: 2-step verification
If you want to add an extra layer of security to your account, we highly recommend that you enable 2-step verification. To enforce 2-step verification on your DSM account and Synology Account, you’ll need a mobile device and an authenticator app that supports the Time-based One-Time Password (TOTP) protocol. Signing in will require both your user credentials and a time-limited 6-digit code retrieved from Microsoft Authenticator, Authy, or other authenticator apps to prevent unauthorized access.
For Synology Account, if you lost your phone with the authenticator app*, you can use the backup codes provided during the 2-step authentication setup to sign in. It is important to keep these codes safe by downloading it somewhere or printing them out. Remember to keep these codes safe but accessible.
On DSM, if you lose your authenticator, you can reset 2-step verification as a last resort. Users belonging to the administrators group can reset the configuration.
If all administrator accounts are no longer accessible, you will need to reset the credentials and network settings on your device. Hold the hardware RESET button on your NAS for around 4 seconds (you’ll hear a beep) and then launch Synology Assistant to reconfigure your device.**
* Some authentication apps support 3rd party account-based backup and restoration methods. Evaluate your security requirements versus convenience and disaster recovery options.
** SHA, VMM, encrypted shared folder automount, multiple security settings, user accounts, and port settings will be reset.
 Tip 8: Change default ports
Tip 8: Change default ports
Though changing DSM’s default HTTP (5000) and HTTPS (5001) ports to custom ports cannot prevent targeted attacks, it can deter common threats that only attack predefined services. To change the default ports, go to Control Panel > Network > DSM Settings and customize the port numbers. It is also a good idea to change the default SSH (22) port if you regularly use shell access.
You can also deploy a reverse proxy to reduce potential attack vectors to only specific web services for increased security. A reverse proxy acts as an intermediary for communications between an (usually) internal server and remote clients, hiding certain information about the server, such as its actual IP address.
 Tip 9: Disable SSH/telnet when not in use
Tip 9: Disable SSH/telnet when not in use
If you’re a power user that often requires shell access, remember to turn off SSH/telnet when not in use. As root access is enabled by default and SSH/telnet only supports sign-ins from admin accounts, hackers may brute-force your password to gain unauthorized access to your system. If you need to have terminal service to be available at all times, we recommend that you set a strong password and change the default SSH port number (22) to increase security. You can also consider leveraging VPNs and limiting SSH access to only local or trusted IPs.
 Tip 10: Encrypt shared folders
Tip 10: Encrypt shared folders
DSM supports AES-256 encryption of your shared folders to prevent data extraction from physical threats. Admins can encrypt newly created and existing shared folders.
To encrypt existing shared folders, go to Control Panel > Shared Folder and Edit the folder. Set up an encryption key under the Encryption tab and DSM will start encrypting the folder. We highly recommend saving the key file generated in a secure location, as encrypted data cannot be recovered without the passphrase used or the key file.
Bonus tip: Data Integrity
Data security is inextricably linked with the consistency and accuracy of your data — data integrity. Data security is a prerequisite for data integrity, as unauthorized access could lead to data tampering or data loss, rendering your critical data useless.
There are two measures you can take to ensure the accuracy and consistency of your data: enabling data checksum and running S.M.A.R.T. tests regularly. We’ve written about these two security methods in our previous blog posts — go check them for more information.
More important than ever
Online threats are always evolving and data security needs to be equally multifaceted. As more connected devices are introduced at home and at work, it becomes easier for cybercriminals to exploit security holes and gain entry into your network. Staying secure is not something you do once and then forget about, it is an ongoing process.
Credit to source, information taken from:
Synology Inc. (2020). Synology: 10 security tips to keep your data safe [online] Synology Inc.
Available at: https://blog.synology.com/10-security-tips-to-keep-your-data-safe/?utm_source=eNews&utm_medium=email [Accessed 16 March 2020].


